"Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords and analyzing routing protocols. The program does not exploit any software vulnerabilities or bugs that could not be fixed with little effort. It covers some security aspects/weakness present in protocol's standards, authentication methods and caching mechanisms; its main purpose is the simplified recovery of passwords and credentials from various sources, however it also ships some "non standard" utilities for Microsoft Windows users." read more...
Wednesday, May 6, 2020
Cain And Abel
How To Create Fake Email Address Within Seconds

How To Create Fake Email Address Within Seconds
Email address is a type of identification by which an email receiver identifies the person who sends mail to him/her. That's why while creating an email address you need to enter your personal details that must be valid. However, what if we tell you that you can create an email address that doesn't require any validation of personal details and that email address gets permanently deleted after your work is done. So here we have a method To Create Fake Email Address. By this, you can create a fake email address that will get auto-deleted after ten minutes. Just follow the below steps to proceed.
Note: The method we are discussing is just for a known purpose and should not be used for any illegal purposes, as we will be not responsible for any wrongdoing.
How To Create Fake Email Address Within Seconds
The method of creating a fake email address is very simple and easy as these are based on online websites that will provide you a free email address without taking any personal details from you.
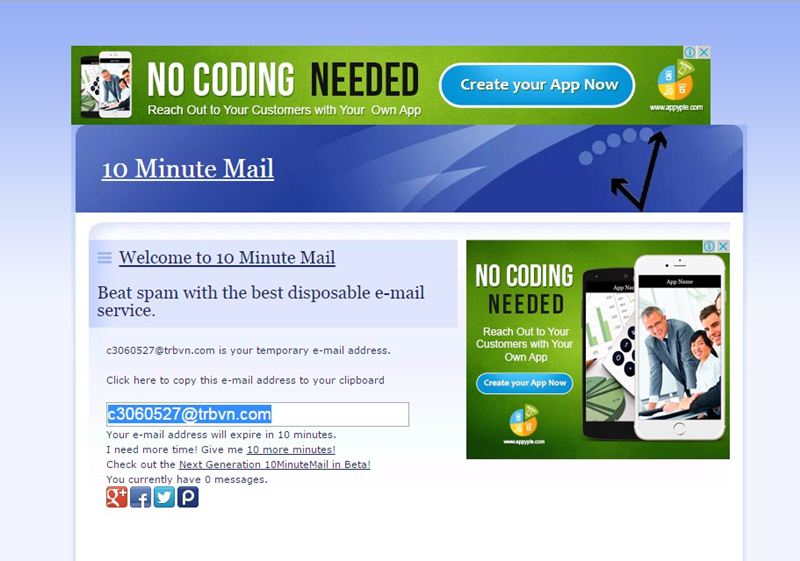
#1 10 Minute Mail
10 Minute Mail will provide you a temporary e-mail address. Any e-mails sent to that address will show automatically on the web page. You can read them, click on links, and even reply to them. The email address will expire after 10 minutes.
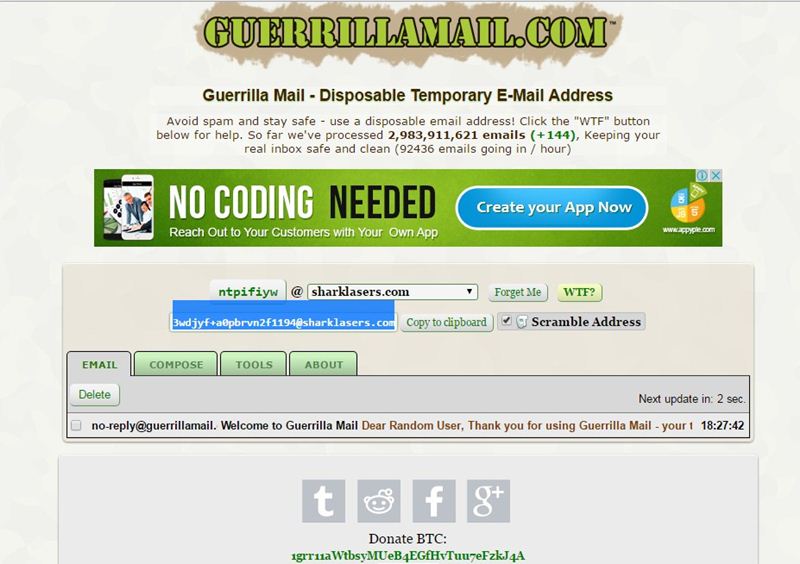
#2 GuerrillaMail
It is one of the most user-friendly ones out there, with this, you can get disposable email ID easily. You need to enter the details, and the fake email ID will be generated. Moreover, this also lets you send emails with attachment up to 150MB. You will be provided with a temporary email address which you can use to verify some websites which require the email address.
#3 Mailinator
Mailinator is a free, Public, Email System where you can use any inbox you want. You will be given a Mailinator address which you can use anytime a website asks for an email address. The public emails you will receive will be auto-deleted after few hours of receiving.
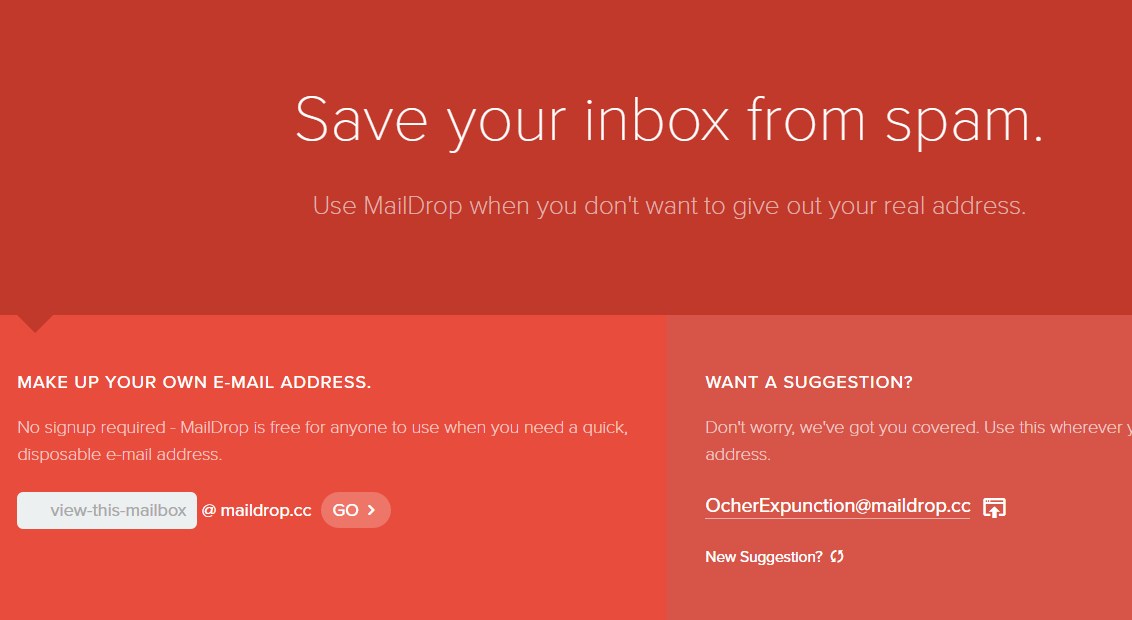
#4 MailDrop
Maildrop is a great idea when you want to sign up for a website but you are concerned that they might share your address with advertisers. MailDrop is powered by some of the spam filters created by Heluna, used in order to block almost all spam attempts before they even get to your MailDrop inbox. This works the same way like Mailinator in which you will be given a temporary Email address which you can use to verify sites etc.
#5 AirMail
AirMail is a free temporary email service, you are given a random email address you can use when registering to new websites or test-driving untrusted services. All emails received by AirMail servers are displayed automatically in your online browser inbox.
Tuesday, May 5, 2020
Mythbusters: Is An Open (Unencrypted) WiFi More Dangerous Than A WPA2-PSK? Actually, It Is Not.
Introduction
Whenever security professionals recommend the 5 most important IT security practices to average users, one of the items is usually something like: "Avoid using open Wifi" or "Always use VPN while using open WiFi" or "Avoid sensitive websites (e.g. online banking) while using open WiFI", etc.
What I think about this? It is bullshit. But let's not jump to the conclusions. Let's analyze all risks and factors here.
During the following analysis, I made two assumptions. The first one is that we are comparing public WiFi hotspots with no encryption at all (referred to as Open), and we compare this to public WiFi hotspots with WPA2-PSK (and just hope WEP died years before). The other assumption is there are people who are security-aware, and those who just don't care. They just want to browse the web, access Facebook, write e-mails, etc.
The risks
Let's discuss the different threats people face using public hotspots, compared to home/work internet usage:
1. Where the website session data is not protected with SSL/TLS (and the cookie is not protected with secure flag), attackers on the same hotspot can obtain the session data and use it in session/login credentials stealing. Typical protocols affected:
- HTTP sites
- HTTPS sites but unsecured cookie
- FTP without encryption
- IMAP/SMTP/POP3 without SSL/TLS or STARTTLS
2. Attackers can inject extra data into the HTTP traffic, which can be used for exploits, or social engineer attacks (e.g. update Flash player with our malware) – see the Dark Hotel campaign
3. Attackers can use tools like SSLStrip to keep the user's traffic on clear text HTTP and steal password/session data/personal information
4. Attackers can monitor and track user activity
5. Attackers can directly attack the user's machine (e.g. SMB service)
WPA2-PSK security
So, why is a public WPA2-PSK WiFi safer than an open WiFi? Spoiler alert: it is not!
In a generic public WPA2-PSK scenario, all users share the same password. And guess what, the whole traffic can be decrypted with the following information: SSID + shared password + information from the 4-way handshake. https://wiki.wireshark.org/HowToDecrypt802.11
If you want to see it in action, here is a nice tutorial for you
 |
| Decrypted WPA2-PSK traffic |
Any user having access to the same WPA2-PSK network knows this information. So they can instantly decrypt your traffic. Or the attackers can just set up an access point with the same SSID, same password, and stronger signal. And now, the attacker can instantly launch active man-in-the-middle attacks. It is a common belief (even among ITSEC experts) that WPA2-PSK is not vulnerable to this attack. I am not sure why this vulnerability was left in the protocol, if you have the answer, let me know. Edit (2015-08-03): I think the key message here is that without server authentication (e.g. via PKI), it is not possible to solve this.
Let me link here one of my previous posts here with a great skiddie tool:
To sum up, attackers on a WPA2-PSK network can:
- Decrypt all HTTP/FTP/IMAP/SMTP/POP3 passwords or other sensitive information
- Can launch active attacks like SSLStrip, or modify HTTP traffic to include exploit/social engineer attacks
- Can monitor/track user activity
The only difference between open and WPA2-PSK networks is that an open network can be hacked with an attacker of the skill level of 1 from 10, while the WPA2-PSK network needs and an attacker with a skill level of 1.5. That is the difference.
The real solutions
1. Website owners, service providers should deploy proper (trusted) SSL/TLS infrastructure, protect session cookies, etc. Whenever a user (or security professional) notices a problem with the quality of the service (e.g. missing SSL/TLS), the service provider has to be notified. If no change is made, it is recommended to drop the service provider and choose a more secure one. Users have to use HTTPS Everywhere plugin.
2. Protect the device against exploits by patching the software on it, use a secure browser (Chrome, IE11 + enhanced protection), disable unnecessary plugins (Java, Flash, Silverlight), or at least use it via click-to-play. Also, the use of exploit mitigations tools (EMET, HitmanPro Alert, Malwarebytes AntiExploit) and a good internet security suite is a good idea.
4. Don't click blindly on fake downloads (like fake Flash Player updates)
5. The benefits of a VPN is usually overestimated. A VPN provider is just another provider, like the hotspot provider, or the ISP. They can do the same malicious stuff (traffic injecting, traffic monitoring, user tracking). Especially when people use free VPNs. And "Average Joe" will choose a free VPN. Also, VPN connections tend to be disconnected, and almost none of the VPN providers provide fail secure VPNs. Also, for the price of a good VPN service you can buy a good data plan and use 4G/3G instead of low-quality public hotspots. But besides this, on mobile OSes (Android, iOS, etc.) I strongly recommend the use of VPN, because it is not practically feasible to know for users which app is using SSL/TLS and which is not.
6. Use a location-aware firewall, and whenever the network is not trusted, set it to a Public.
7. In a small-business/home environment, buy a WiFi router with guest WiFi access possibility, where the different passwords can be set to guest networks than used for the other.
Asking the question "Are you using open WiFi?", or "Do you do online banking on open WiFi?" are the wrong questions. The good questions are:
- Do you trust the operator(s) of the network you are using?
- Are the clients separated?
- If clients are not separated, is it possible that there are people with malicious intent on the network?
- Are you security-aware, and are you following the rules previously mentioned? If you do follow these rules, those will protect you on whatever network you are.
And call me an idiot, but I do online banking, e-shopping, and all the other sensitive stuff while I'm using open WiFi. And whenever I order pizza from an HTTP website, attackers can learn my address. Which is already in the phone book, on Facebook, and in every photo metadata I took with my smartphone about my cat and uploaded to the Internet (http://iknowwhereyourcatlives.com/).
Most articles and research publications are full of FUD about what people can learn from others. Maybe they are just outdated, maybe they are not. But it is totally safe to use Gmail on an open WiFi, no one will be able to read my e-mails.
PS: I know "Average Joe" won't find my blog post, won't start to read it, won't understand half I wrote. But even if they do, they won't patch their browser plugins, pay for a VPN, or check the session cookie. So they are doomed to fail. That's life. Deal with it.
Read more
WHAT IS ETHICAL HACKING
Ethical hacking is identifying weakness in computer system and/or computer networks and coming with countermeasures that protect the weakness.
Ethical hackers must abide by the following rules-
1-Get written permission from the owner of the computer system and/or computer network before hacking.
2-Protect the privacy of the organisation been hacked etc.
Ethical Hacking and Ethical Hacker are terms used to describe hacking performed by a company or individual to help identity potential threats on a computer or network.
Ethical hackers must abide by the following rules-
1-Get written permission from the owner of the computer system and/or computer network before hacking.
2-Protect the privacy of the organisation been hacked etc.
Ethical Hacking and Ethical Hacker are terms used to describe hacking performed by a company or individual to help identity potential threats on a computer or network.
An Ethical Hacker attempts to byepass system security and search for any weak point that could be exploited by Malicious Hackers.
More info
INTERCEPT - Policy As Code Static Analysis Auditing
Stupidly easy to use, small footprint Policy as Code subsecond command-line scanner that leverages the power of the fastest multi-line search tool to scan your codebase. It can be used as a linter, guard rail control or simple data collector and inspector. Consider it a weaponized ripgrep. Works on Mac, Linux and Windows.
How it works
- intercept binary
- policies yaml file
- (included) latest ripgrep binary
- (optional) exceptions yaml file
Use cases
- Simple and powerful free drop-in alternative for Hashicorp Sentinel if you are more comfortable writing and maintaining regular expressions than using a new custom policy language.
- Do you find Open Policy Agent rego files too much sugar for your pipeline?
- Captures the patterns from git-secrets and trufflehog and can prevent sensitive information to run through your pipeline. (trufflehog regex)
- Identifies policy breach (files and line numbers), reports solutions/suggestions to its findings making it a great tool to ease onboarding developer teams to your unified deployment pipeline.
- Can enforce style-guides, coding-standards, best practices and also report on suboptimal configurations.
- Can collect patterns or high entropy data and output it in multiple formats.
- Anything you can crunch on a regular expression can be actioned on.
Latest Release :
# Standard package (intercept + ripgrep) for individual platforms
-- intercept-rg-linux.zip
-- intercept-rg-macos.zip
-- intercept-rg-win.zip
# Clean package (intercept only) for individual platforms
-- core-intercept-linux.zip
-- core-intercept-macos.zip
-- core-intercept-win.zip
# Full package (intercept + ripgrep) for all platforms
-- x-intercept.zip
# Package needed to fully use the Makefile
-- setup-buildpack.zip
# Package of the latest compatible release of ripgrep (doesn't include intercept)
-- i-ripgrep-linux.zip
-- i-ripgrep-macos.zip
-- i-ripgrep-win.zipDownload the standard package for your platform to get started
Used in production
INTERCEPT was created to lint thousands of infra deployments a day with minor human intervention, the first MVP been running for a year already with no reported flaws. Keep in mind INTERCEPT is not and does not pretend to be a security tool. It's easy to circumvent a regex pattern once you know it, but the main objective of this tool is to pro-actively help the developers fix their code and assist with style suggestions to keep the codebase clean and avoid trivial support tickets for the uneducated crowd.
Inspired by
Standing on the shoulders of giants
Why ripgrep ? Why is it fast?
- It is built on top of Rust's regex engine. Rust's regex engine uses finite automata, SIMD and aggressive literal optimizations to make searching very fast. (PCRE2 support) Rust's regex library maintains performance with full Unicode support by building UTF-8 decoding directly into its deterministic finite automaton engine.
- It supports searching with either memory maps or by searching incrementally with an intermediate buffer. The former is better for single files and the latter is better for large directories. ripgrep chooses the best searching strategy for you automatically.
- Applies ignore patterns in .gitignore files using a RegexSet. That means a single file path can be matched against multiple glob patterns simultaneously.
- It uses a lock-free parallel recursive directory iterator, courtesy of crossbeam and ignore.
Benchmark ripgrep
| Tool | Command | Line count | Time |
|---|---|---|---|
| ripgrep (Unicode) | rg -n -w '[A-Z]+_SUSPEND' | 450 | 0.106s |
| git grep | LC_ALL=C git grep -E -n -w '[A-Z]+_SUSPEND' | 450 | 0.553s |
| The Silver Searcher | ag -w '[A-Z]+_SUSPEND' | 450 | 0.589s |
| git grep (Unicode) | LC_ALL=en_US.UTF-8 git grep -E -n -w '[A-Z]+_SUSPEND' | 450 | 2.266s |
| sift | sift --git -n -w '[A-Z]+_SUSPEND' | 450 | 3.505s |
| ack | ack -w '[A-Z]+_SUSPEND' | 1878 | 6.823s |
| The Platinum Searcher | pt -w -e '[A-Z]+_SUSPEND' | 450 | 14.208s |
Tests
Test Suite runs with venom
venom run tests/suite.ymlVulnerabilities
Scanned with Sonatype Nancy
Audited dependencies:41,Vulnerable:0via KitPloit
This article is the property of Tenochtitlan Offensive Security. Verlo Completo --> https://tenochtitlan-sec.blogspot.com
More articles
Friday, May 1, 2020
Falcons, Spears And Revenants, Oh My
I finished the first of the six Falcon turrets last Friday right before NEAT. The next six are going to be magnetised so I can swap them out for Fire Prism turrets (haven't started on those yet though).



I also did some conversion work earlier this week on my Revenants. I did some leg swaps to add some pose variety and magnetized the weapons. I have some Vibrocannon arm conversions to work on and a bit of puttying to do before these see paint.

Finally, I finished up the lances and gems on the Shining Spears last night, and put on their decals as well. They'll need a bit of touch up and bases edges before they get top coated.


A Note On "Standard" Player Powers
In a few recent TMG games I've worked on (Harvest, Pioneer Days, and Old West Empresario) I thought a lot about how to do player powers in the game.
In Harvest, the "standard" side of each player board (recommended for first time players) is Wil Plantsomdil, who starts with a basic spread of resources, and gets a big VP bonus at game end. The intent was to allow a new player to play in a game with experienced players, not have to wrestle with a player power while also learning the game, and still get a competitive score. In that game, I wouldn't blame "experienced games" for skipping Wil Plantsomdil and going straight for the "real" player powers. However, I thought we could do better...
In Pioneer Days and Old West Empresario, the Standard Pioneer / Standard Empresario abilities are not just a dumbed down power meant for newbie players. Rather we took one of the more well-rounded or straightforward of the powers we were developing, one which we thought would make for a good first experience, and made that the "standard" power.
The rules for both of those games say to deal 2 characters to each player and let them choose between one unique ability, the other, or the standard ability on the back side. While we recommend that first time players choose the standard ability, we worked hard to balance them all so that the standard power is on par with the unique ones, giving each player 3 solid options.
I fear that players will assume that "standard" implies "boring," automatically skip the "standard" ability as if it didn't exist, and therefore miss out on one of the fun player powers.
Hopefully we can break them of this habit. I played a game of Old West Empresario the other day and intentionally chose the Standard Empresario ability, and I did better than I've done in a long time!
TL;DR: In Pioneer Days, Old West Empresario, and any future TMG title I work on, don't look at the standard player power as "lesser" -- it's designed to be on par with the rest of the player powers!
In Harvest, the "standard" side of each player board (recommended for first time players) is Wil Plantsomdil, who starts with a basic spread of resources, and gets a big VP bonus at game end. The intent was to allow a new player to play in a game with experienced players, not have to wrestle with a player power while also learning the game, and still get a competitive score. In that game, I wouldn't blame "experienced games" for skipping Wil Plantsomdil and going straight for the "real" player powers. However, I thought we could do better...
In Pioneer Days and Old West Empresario, the Standard Pioneer / Standard Empresario abilities are not just a dumbed down power meant for newbie players. Rather we took one of the more well-rounded or straightforward of the powers we were developing, one which we thought would make for a good first experience, and made that the "standard" power.
The rules for both of those games say to deal 2 characters to each player and let them choose between one unique ability, the other, or the standard ability on the back side. While we recommend that first time players choose the standard ability, we worked hard to balance them all so that the standard power is on par with the unique ones, giving each player 3 solid options.
I fear that players will assume that "standard" implies "boring," automatically skip the "standard" ability as if it didn't exist, and therefore miss out on one of the fun player powers.
Hopefully we can break them of this habit. I played a game of Old West Empresario the other day and intentionally chose the Standard Empresario ability, and I did better than I've done in a long time!
TL;DR: In Pioneer Days, Old West Empresario, and any future TMG title I work on, don't look at the standard player power as "lesser" -- it's designed to be on par with the rest of the player powers!
Subscribe to:
Posts (Atom)